
Intrusion Detection System
Functions:
Efficiently intercept internet packets and navigate through the packet headers.
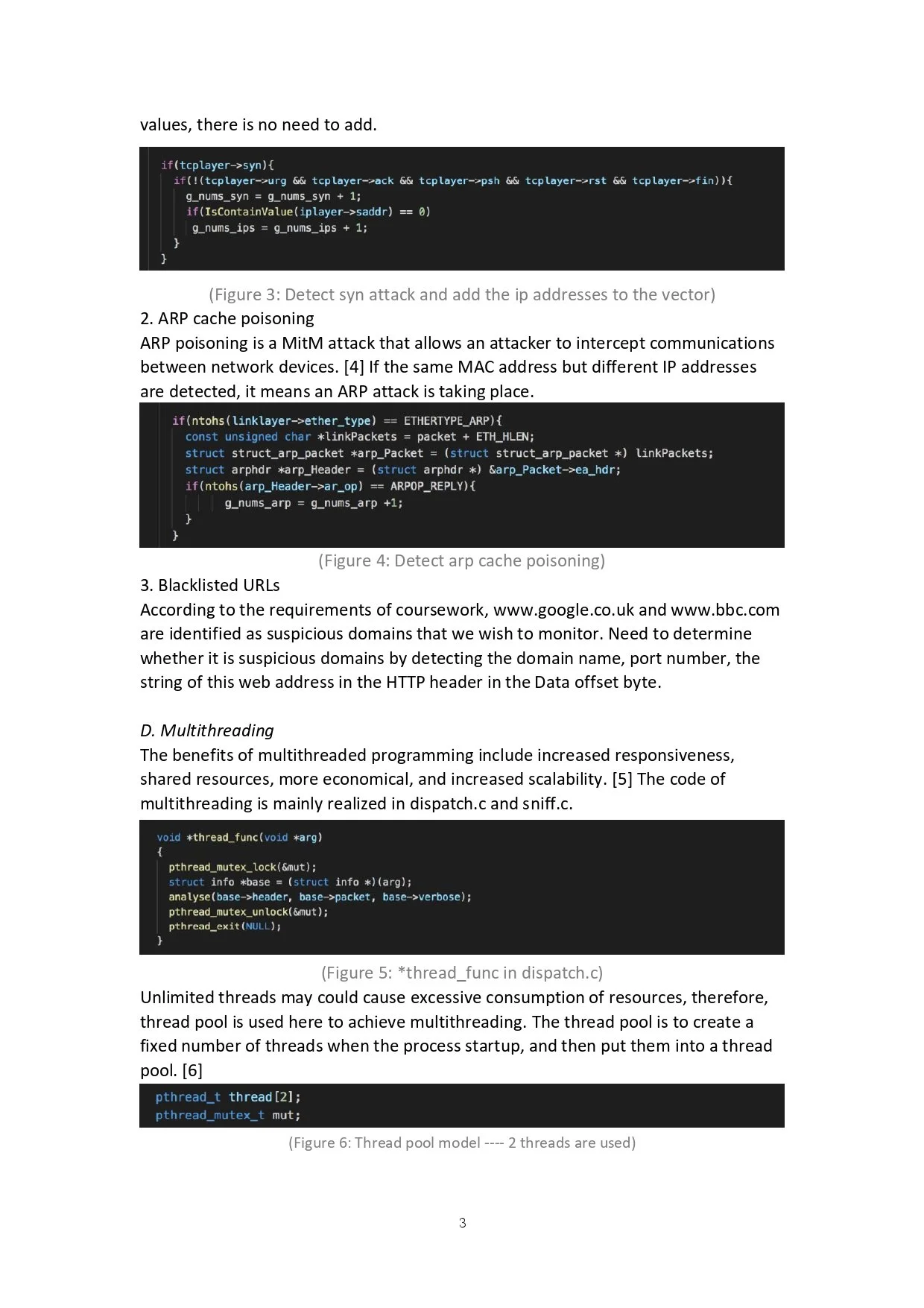
Detect specific malicious activities (e.g., SYN attacks, ARP cache Poisoning attack, Blacklisted URL detection).
Implement a threading strategy to allow efficient detection of the attacks when there is high traffic.
Operating Systems and Computer Networks
The goal of this project is to detect potentially malicious traffic in high-throughput networks. It implements multithreading and detects the SYN flooding attack, ARP cache poisoning, and Blacklisted URLs.
My Testing Report (Final Score: 98/100) ——— Threading strategy and implementation



Specification of Malicious Packets
-
This attack is achieved when a server listening on a TCP socket is flooded with TCP SYN packets (packets whose SYN bit is set to 1 and all other flag bits are set to 0). For each received SYN packet, the server opens a TCP connection, allocates some resources, replies with a SYN-ACK packet and then waits for an ACK from the sender. However, the malicious sender does not send the ACK. This creates a half-open TCP connection at the server which occupies some resources. As the attacker sends many such SYN packets, the server resources get used up and as a result, legitimate connection requests are dropped. This is a form of denial-of-service attack. In most cases, the attacker generates the SYN packets from spoofed IP addresses. Spoofed IP addresses are randomly generated and do not correspond to the attacker's real IP address. They are used to hide the attacker's own identity.
-
The Address Resolution Protocol (ARP) is used by systems to construct a mapping between network layer (Media Access Control) and link layer (Internet Protocol) addresses. Consider a simple scenario: two systems share a network - dcs_laptop has IP address 192.168.1.68 and is trying to communicate with broadband_router at 192.168.1.1. To achieve this, dcs_laptop broadcasts an ARP request asking for the MAC address of the node at 192.168.1.1. When broadband_router sees this message it responds with its MAC address. dcs_laptop will cache this address for future use and then use it to establish a connection.
-
Intrusion detection systems typically watch traffic originating from the network they protect in addition to attacks coming from outside. This can allow them to detect the presence of a virus trying to connect back to a control server for example, or perhaps monitor any attempts to smuggle sensitive information to the outside world. For this exercise, we have identified www.google.co.uk and www.bbc.com as a suspicious domains that we wish to monitor. Specifically, we wish to be alerted when we see HTTP traffic being sent to these domains.
GitHub Repositories: https://github.com/YW-2022/project3